Example Phish 015
What to learn from this phish...
In short, before entering credentials, look at the web address and make sure the site you are on "matches" with the URL. Also, please take a look at phish011 as it is an almost identical scam.
Here is the original email that you might receive:

The link has two sets of three slashes, right? The first is the cudasvc (your company email filter) that attemps to verify links for us against a known bad links database. This is not reliable, but another layer that could help. The second set of three slashes is the actual link in the highlighted area.
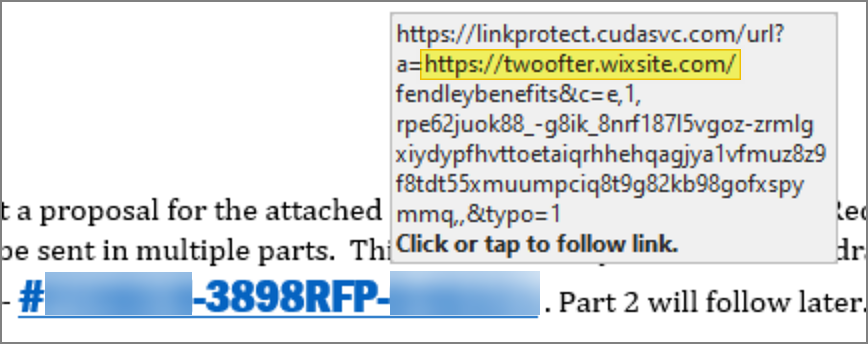
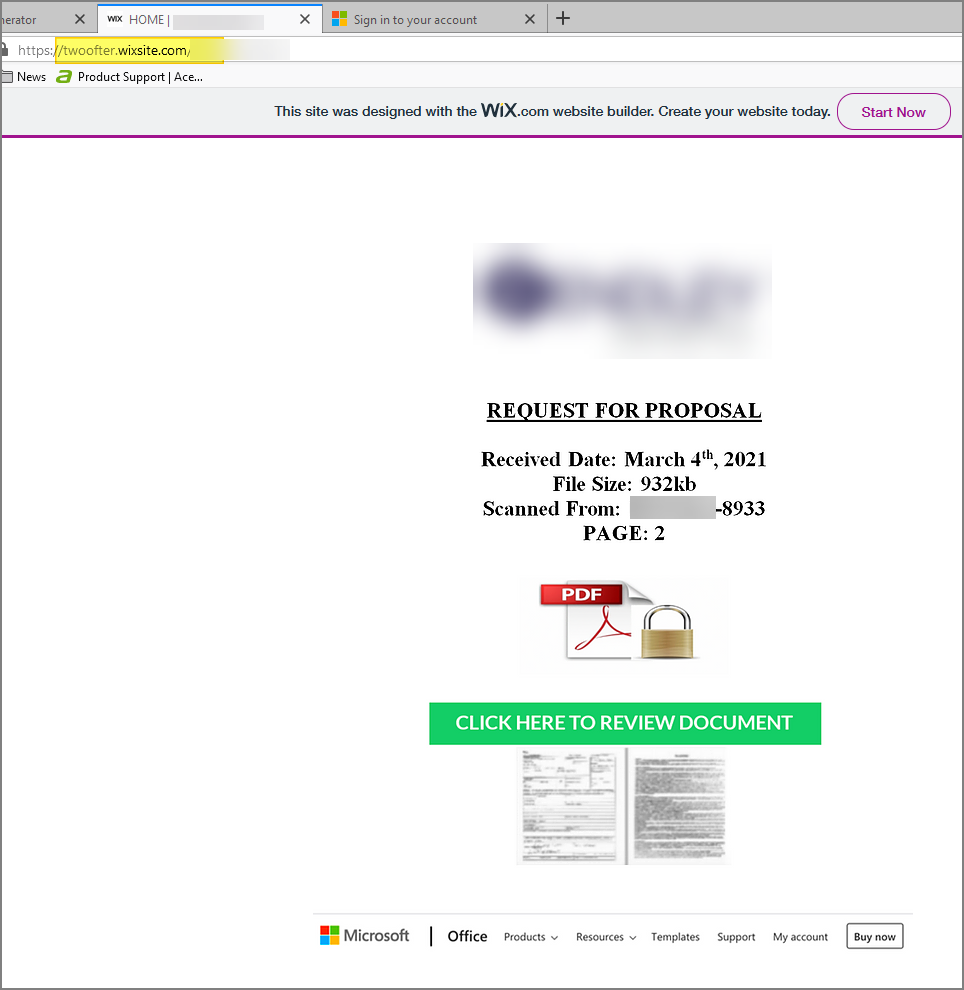
If you follow the link you get to a seemingly legitimate webpage. Wixsite.com is an online website builder where users with little web development skills can generate a website. While not a bad website on it's own, this is suspicious as most file hosting services would not be on Wixsite.com
Furthermore, the PDF and Lock icons are a bit unprofessional looking and stand out a bit too much. Most proper, secure sites would not have those icons in that prominent of a spot of a page. They are really trying to make you feel "safe".
The preview icon is also something that is commonly used in scam website.
Lastly, the "links" to Microsoft at the bottom of the page are not multiple links. They are an image of all those links. The hacker was too lazy to reproduce the navigation menu, so they simply took a screenshot of the menu and placed it at the bottom of the page to make it look more authentic.
Finally, you are signing into Microsoft as the sign-in screen displays, but the URL/Web address reveal you are on a site with domain backblazeb2.com. This is suspicious and incorrect. The actual Microsoft login screen is on microsoftonline.com!
If you enter credentials on this page and the subsequent page, your username and password will be sent to the attackers and you will get a invalid login screen.
