Example Phish 007
Quote
“There are always new places to go fishing. For any fisherman, there’s always a new place, always a new horizon.” – Jack Nicklaus
What to learn from this phish...

The links (1), (2), and (3) all go to their intended target, sync.com. (Sync.com is a legitimate file sharing service.)
There are no misspellings or anything that would give you any clues - everything just looks right.
The truth is, this actually is a legitimate email from Sync.com.
The scam is actually in the file that was sent!
To stop the scam at this point is hard, but not impossible. The only defense you have, is to constantly think: Why did this person send me a file with this title at this time?
It may not be enough, but it just might prompt you to take evasive action. Try getting in the habit of asking yourself this. If something isn’t quite right, call the sender. It might seem like a lot to do, but the truth is, if you eventually fall for the scam, you’re going to call the sender anyway and it can be ten if not hundreds of times less than the possible downtime due to the scam.
After clicking the link (#2) you would have been presented with the screen below:
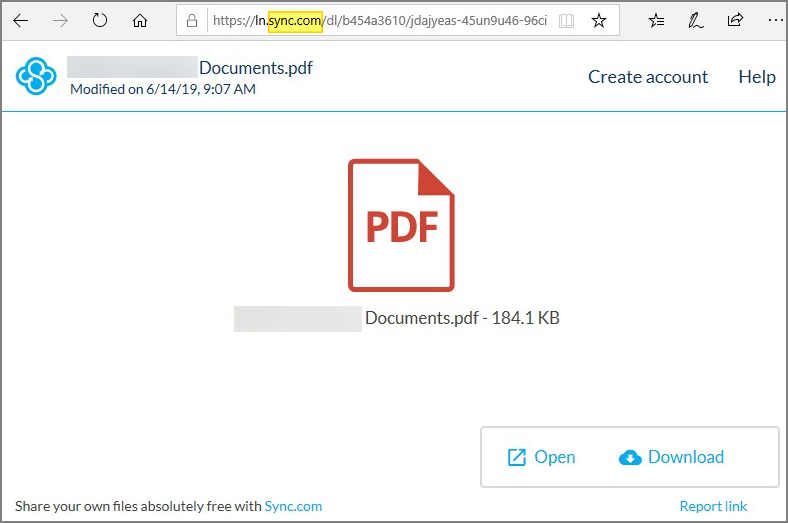
Again, this is a legitimate page at this point. It’s still part of Sync.com’s system. You can see by the address bar that you are where the link said you would go. If you hover over the links on this page you would find they are all legitimate.
If you made it to this point, there is nothing that would stop you from opening or downloading the file. Perhaps the title…
After opening the file you would see what’s in the image below:
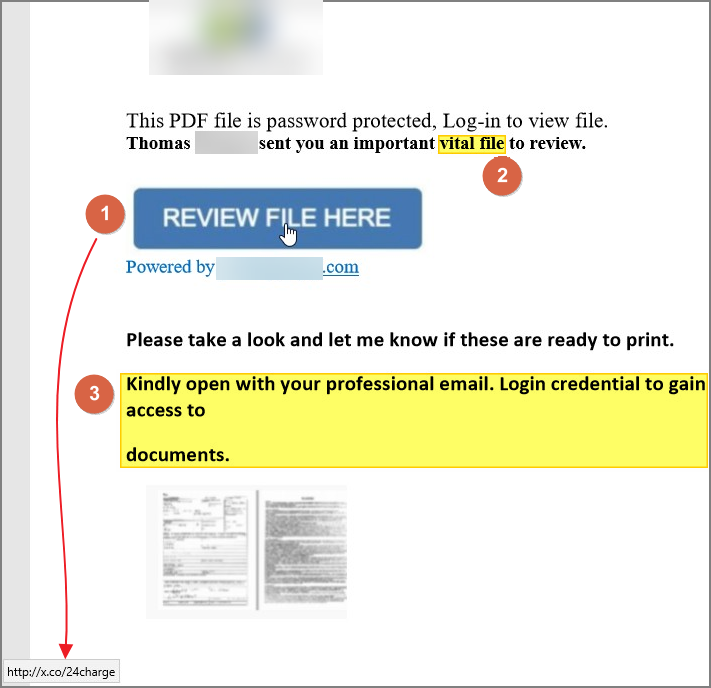
It looks pretty good. The logo at the top, the thumbnails of the document at the bottom, but there are many clues that should cause your Spidey Sense to Tingle!
(1) First, the big, blue button.
-
You should not have to click buttons in PDF files for anything. Also, notice where you would go if you clicked the link? Doesn’t that look phishy?
http://x.co/24charge -
First off, you are being asked to review an important, “vital” file yet you are being taken to an unsecure website! Notice there is no “S” after the HTTP.
-
Second, the target of that link has nothing to do with anything: X.CO is the target. I’ve never needed to go to a website named “X” and I never need to use the “.CO” top-level domain. Usually it’s .com, or .net, org, etc.
(2) Second, how often do people say this is an important, vital file for you to review? Maybe in a different context.
(3) Third, this sentence just isn’t correct. Also, why do I need to use my email credentials to open the document?
At this point if you continue clicking the link you would have been taken to the website. On that website you would have been asked to authenticate with your “Professional Email Login Credential”, OR for your convenience you could have used any one of your favorite logins to gain access: you could have logged on via, Gmail, Facebook, Twitter, etc. etc.
Takeaways
This attempt would more than likely get blocked after the button is clicked by web filtering (assuming good security), but if not, the attacker could learn your username and password. Hopefully, it would not be your company credentials because everyone knows not to use those anywhere except for approved company systems, but what if you forgot?
- What if you logged on with your personal account in a similar scenario?
- What if you use the same password for your personal account as your other home accounts?
- What if the attacker takes your credentials and presents some documents stollen from the sender that pertain to your company?
- When would you realize it was a scam?
We need to be constantly vigilant and learning how to protect oneself online and why there is no substitue for good training - in a company or at home, you are the last line of defense!