Phishing
Important
If you believe you have received a phishing email, you need to stop and not proceed with any action like clicking links or entering sensitive information or even clicking [X] to close a window. Simply stop all actions and report it to your IT/Security/Support Department immediatly.
Phishing is a cybercrime in which a target or targets are contacted by email, telephone or text message by someone posing as a legitimate institution to lure individuals into providing sensitive data such as personally identifiable information, banking and credit card details, and passwords.
The information is then used to access important accounts and can result in identity theft and financial loss.
Common Features of Phishing Emails
-
Too Good To Be True - Lucrative offers and eye-catching or attention-grabbing statements are designed to attract people’s attention immediately. For instance, many claim that you have won an iPhone, a lottery, or some other lavish prize. Just don't click on any suspicious emails. Remember that if it seems to good to be true, it probably is!
-
Sense of Urgency - A favorite tactic amongst cybercriminals is to ask you to act fast because the super deals are only for a limited time. Some of them will even tell you that you have only a few minutes to respond. When you come across these kinds of emails, it's best to just ignore them. Sometimes, they will tell you that your account will be suspended unless you update your personal details immediately. Most reliable organizations give ample time before they terminate an account and they never ask patrons to update personal details over the Internet. When in doubt, visit the source directly rather than clicking a link in an email.
-
Links - A link may not be all it appears to be. Hovering over a link shows you the actual URL where you will be directed upon clicking on it. It could be completely different or it could be a popular website with a misspelling, for instance www.bankofarnerica.com - the 'm' is actually an 'r' and an 'n', so look carefully.
-
Attachments - If you see an attachment in an email you weren't expecting or that doesn't make sense, don't open it! They often contain payloads like ransomware or other viruses. The only file type that is always safe to click on is a .txt file.
-
Unusual Sender - Whether it looks like it's from someone you don't know or someone you do know, if anything seems out of the ordinary, unexpected, out of character or just suspicious in general don't click on it!

What You Must Do
-
In short, always do four (4) simple things:
- Don’t just click.
- Investigate the link and identify the target.
- Trust your gut.
- Report anything out of the ordinary or you feel is suspicious.
-
This applies to all types of links whether it’s in an email or on a webpage or when you are doing a search.
-
It’s very easy to forget to do these things during the course of a busy work day, but just take a moment, that’s all it takes.
-
In many cases you may need to call the person sending you the email to verify the email is legitimate.
-
In most cases, you don't need to click links in emails as you can go directly to the website. For example, if you receive an email from Amazon.com asking to click a link to update your profile, you are much safer FIRST browsing to Amazon.com and logging in to your account and then making changes, therefor bypassing any links in an email.
Links or URLs
Main Components
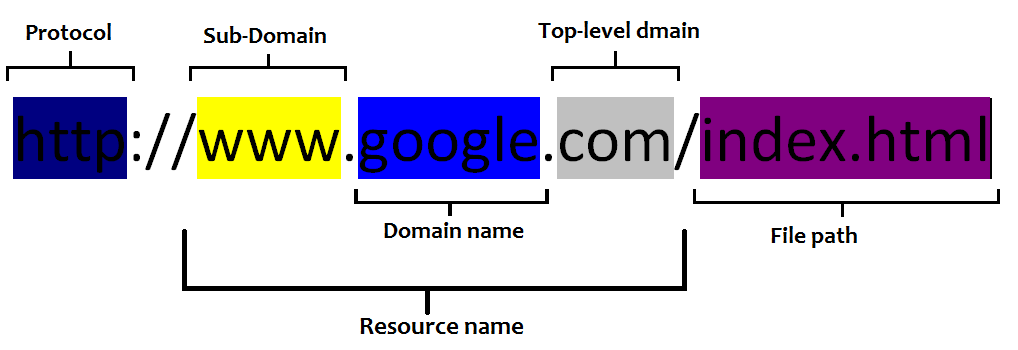
Three slashes and you're out!
Well, actually you're safe... but this method will help you in almost all cases identify a bad link from a good one.
Because emails can come from compromised accounts of someone you do business with on a regular basis, the email by itself is no longer a good way to judge if the message is a scam.
The only way is to understand the link the scammer wants you to visit.
This method makes it really easy and fast to understand a link and better determine a good one from a bad one:
Example 1

- In any link or web address count the first three forward slashes. Numbers 1, 2 & 3 above...
- Starting at the third slash, work backwards to the first dot. The red underline. This is the ".com" part of the address or Top Level Domain, like .net, .us, .org.
- If you work further backwards, that's the domain, or target of the link.
- In the example above,
criticismwaitlist0k112w.comis the target - this is not a common domain.
Example 2
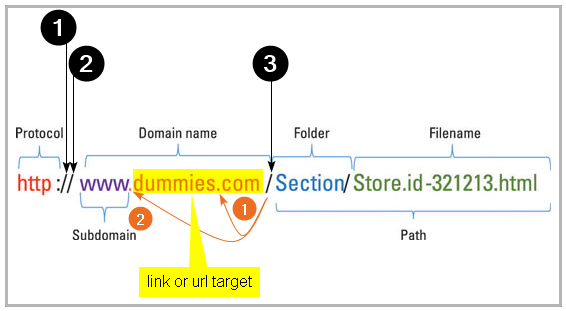
- Count the first three forward slashes. #'s 1, 2 & 3.
- At the third, work backwards (orange arrows) and find the first dot. Orange #1 - that's the Top Level Domain.
- Further back is the word
dummies- this is the target or domain. - In this case
dummies.comis the target.
Subject Lines To Look Out For
A good exercise to go through with your team members is to have them create a list of the top 5 or 10 subject lines they work with on a regular basis that they typically have to take action on.
These subject lines that are almost routine, especially in areas of the business that are repetative in nature like accounts receivables or payroll, etc.
The act of going through this exercise will allow team members to realize that any one of those subject lines could potentially be turned into a phishing emai, and that even though they are familiar, they should always question what they are being asked to do.
| Subject Lines To Look Out For |
|---|
| Personal and Confidental |
| New File Alert |
| Renewal Update |
| Spreadsheet attached |
| Waiting for your response |
| Rush - RFP |
| Overdue Payment |
| Due tomorrow if possible |
| Revised documents |
| Monthly Reporting |
| Quote 001 |
| Claims Status |
Example of Phishing Emails
Please take a visit "down by the pond" to look at all the Phish!